For many of us, Kubernetes is the solution for some of the never-ending microservices application delivery problems, but Kubernetes setup and management come with its own set of challenges. According to a report, there are 9 key Kubernetes challenges. In this blog, I’m focusing on the two primary challenges, which are Security & Networking.
Why is Security becoming such a Big Challenge for Organizations?
Kubernetes security challenges are one of the most critical Kubernetes challenges that businesses usually face while setting up a Kubernetes cluster. It’s mainly because Kubernetes is very complex and highly vulnerable if not monitored properly. As we implement Kubernetes for container orchestration, more and more containers are deployed and due to its distributed nature, hence it gets difficult to investigate which container might have vulnerabilities. As a result, the organization will start to feel the threat of outsiders breaching in.
One of the best examples of this situation: In 2018 Tesla’s Kubernetes admin console (which was not password protected) was breached by Hackers and mining of cryptocurrencies was done by Tesla’s cloud resources on amazon web services (AWS).
What makes Networking a Kubernetes Challenge?
The reason is mainly, that the traditional networking approaches don’t work well with Kubernetes. The larger the scale of Kubernetes deployment, the more challenges will be faced. Some of the most common network Kubernetes challenges faced by users are,
● Complexity challenge
● Addressing challenge
● Multi-tenancy challenge
The complexity challenge is mainly due to the deployment of Kubernetes in more than one cloud infrastructure like private, public, and hybrid. Each cloud infra has its own policy which makes Kubernetes complex across multiple infrastructures. The other complexity challenge that’s faced is due to the usage of mixed workloads – both VM-based and Kubernetes-based deployments, arising from the difference between these architectures.
The addressing challenges that are typically faced are that of static IP addresses and ports getting difficult to be used in Kubernetes for communication because Pods can use an infinite number of IP addresses for let’s say one workload itself. Hence implementing IP-based policies becomes very challenging in the Kubernetes environment.
Last but not the least, the multi-tenancy challenge. This challenge usually arrives in a situation where one Kubernetes environment is shared among multiple workloads. Obviously, when two or more are sharing one thing, there arises these basic challenges such as resource sharing and security. So, there is a high chance if workloads are not properly isolated security breaches in one workload will affect the other workloads in the same environment. Likewise, the same goes for recourse sharing. If not dedicated properly there will be absolute chaos in getting the required resources for each workload.
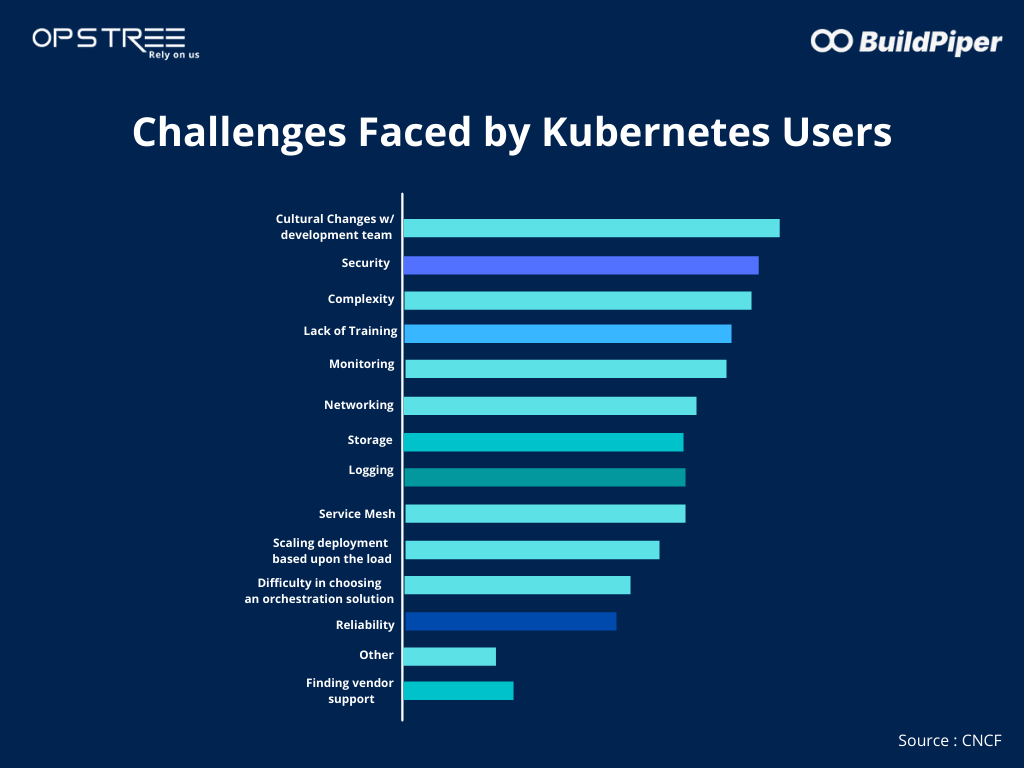
Source: CNCF
Managing these Kubernetes Challenges
Let’s start with solving the Managed Kubernetes security challenges. There are numerous ways to enhance the security of container orchestration using Kubernetes.
- The first method enables RABC (Role-based Access control) So that every user is authenticated and authorized while accessing workloads. This means providing no user, more permission than required to complete their task.
- The second method is managing your secrets more securely by having separate containers like a front-end/user container and a backend container. The front-end container can interact with the backend container but won’t be able to see the private key.
- The third method is enhancing pod security by enabling security modules like AppArmor & SElinux.
When it comes to managing Kubernetes Network challenges,
The first method is implementing a container network interface (CNI) plug-in, which allows Kubernetes to have seamless integration with underlying infrastructure and enables Kubernetes to access applications across different cloud platforms.
The second method is the use of service mesh, which is an infrastructure layer that is inserted right into an app, this layer handles the network-based inter-process communication using APIs. As a result, the communication between containers is fast, smooth & secure.
Also, one of the core advantages of using service mesh is it enables developers to focus more on the primary task and meanwhile operation teams can take responsibility for managing and maintaining a secure connection between applications. All of which will ensure a seamless container orchestration process.
Luckily there are Kubernetes & Microservices application delivery management platforms like BuildPiper that can help in solving all Kubernetes challenges. This platform can do all these activities seamlessly and provide more capabilities to organizations like managed Kubernetes clusters, robust & secure CI/CD pipelines for single or multiple microservices, monitoring of microservices, Infrastructure, Kubernetes clusters, logs etc.
With complete 360-degree observability for managing these and many other challenges with Kubernetes and Microservices application delivery and make it simple, seamless, scalable and cost-optimized!
Subscribe here to get the latest updates on Microservices management, DevOps, Kubernetes deployment & much more!
BuildPiper is an End to End Microservices Delivery Platform.