Enterprises, in the continuous efforts to ripen their cloud-native strategies and to strengthen security in Kubernetes, including what platforms and tools they should use to ensure the safe deployment of cloud-native apps, may benefit from understanding these Kubernetes security challenges! Take a look!
The widespread use of Kubernetes is a testament to enterprises’ faith in their ability not just to handle the complexity of modern app development and modernization initiatives, but to do so at scale. However, Kubernetes being one of the most popular container orchestration platforms, many organizations are still intimidated by its complexity.
Kubernetes solves container issues by providing an extensible, declarative platform that automates the management of containers for high availability, resiliency, and scale. But, Kubernetes deployment is a tough task to handle. Kubernetes is a big, complex, fast-moving, and sometimes confusing platform that requires users to continually learn and acquire new skills.
With such a complex and across-the-board deployment as a Kubernetes cluster, unwanted exposure tends to increase, making Kubernetes vulnerable to security threats and unauthorized access. This ultimately increases the count of hard-to-crack Kubernetes challenges for teams and enterprises.
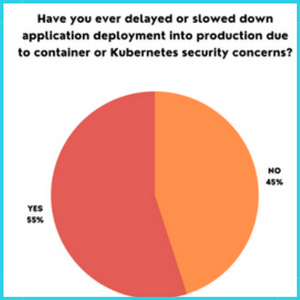
Some organizations are swamped by the security needs that span across multiple aspects of the application life cycle, from development through deployment and maintenance. In a recent survey, 55% of the respondents agreed to have delayed or slowed their application deployment due to container or Kubernetes security concerns.
Image Credits: RedHat Security Survey 2022
Back in 2018, The IBM Cloud Container Registry team wanted to build an image trust service. “Portieris”, an image trust service, is a Kubernetes admission controller to implement a content trust approach. Users can create image security policies for each Kubernetes namespace, or at the cluster level, and implement distinct levels of trust for different images. This way IBM’s intention in offering a managed Kubernetes container service and image registry was to provide a fully secure end-to-end platform for its enterprise customers.
[Good Read: Reducing Kubernetes Costs with Autoscaling]
Here, in this blog, we’ll discuss the top 3 Kubernetes security challenges faced by enterprises and software teams while setting up and deploying Kubernetes clusters. So, let’s take a quick look at this Kubernetes security checklist to avoid security breaches and attacks.
Hardening Kubernetes Cluster to mitigate risks!
Malicious threats can exploit vulnerabilities and misconfigurations in the various components of the Kubernetes architecture, such as the control plane, worker nodes, or containerized applications. Therefore, it’s important for enterprises to apply hardening practices and mitigations to manage associated risks that can thwart their goal to deploy Kubernetes seamlessly.
Organizations can use security benchmarks and a Kubernetes security checklist to assist teams in hardening Kubernetes. The Center for Internet Security provides configuration guidelines to harden systems, including Kubernetes, against evolving cyber threats.
These recommended configuration practices and Kubernetes hardening guidance helps DevSecOps teams in securing a Kubernetes cluster and overcoming complex Kubernetes challenges. However, before applying these measures, organizations must evaluate the impact of certain settings on performance and weigh the risks faced versus the benefits derived.
Some of the ways to harden Kubernetes as suggested in the Cybersecurity Technical Report by the National Security Agency( NSA) include,
- Scan containers and pods to detect vulnerabilities or misconfiguration.
- Use network separation to control the amount of damage, an attack can cause.
- Use firewalls to limit unnecessary network connectivity and use encryption to protect system confidentiality.
- Use robust authentication and authorization to limit access of users and administrators as well as to restrict the attack surface.
- Capture and observe audit logs so that administrators can be alerted to malicious activities.
- Review all Kubernetes settings at regular intervals.
But, Kubernetes hardening isn’t easy. It can become a significant challenge for organizations that don’t have the right skillsets or adequate time to harden Kubernetes on their own. It can be a tedious job to ensure that the desired configuration of the Kubernetes cluster is set and maintained.
Also, it may become overwhelming for organizations to apply and execute these hardening practices in addition to Kubernetes security best practices. In such a scenario, considering a commercial platform for Kubernetes cluster management or Kubernetes security tools that have already accomplished the hardening process, can be the best option to go for, as it saves both time and money.
TO BE CONTINUED!!!!!!!!!!!
Read more about the other Kubernetes security challenges and Kubernetes security best practices in our next blog.